Threat actors are taking advantage of when security professionals are off-duty to stage their ransomware attacks, new research has found. The ThreatDown 2024 State of Ransomware report from Malwarebytes has revealed most incidents in the last year occurred between 1 a.m. and 5 a.m.
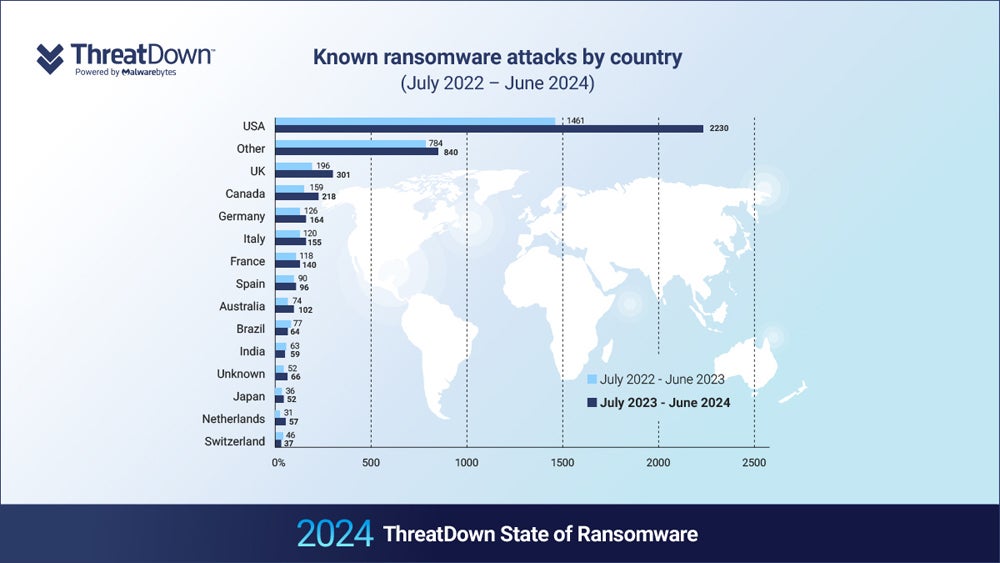
The report’s authors used data from the ThreatDown Managed Detection and Response team to conduct their research. It found that global ransomware attacks increased by 33% in the last year, with the top-targeted countries seeing the largest rises. The U.K. experienced a 67% hike in known attacks, and the U.S. saw a 63% increase.
“The question I ask organizations is ‘do you have someone prepared to stop an attack at 2 a.m. on a Sunday with your existing technology stack and staff resources?’” Chris Kissel, research vice president at IDC’s Security & Trust Products group, said in a press release.
“They may have a tool to pick up the alert on Monday morning, but by then it will be too late. Threat actors are moving fast to compromise networks, download data and deploy ransomware.”
Marcin Kleczynski, founder and CEO of Malwarebytes, added, “Ransomware gangs have time and motivation on their side. They constantly evolve to respond to the latest technologies chasing at their tails.
“We’ve seen this very distinctly over the past year as widespread adoption of technologies like EDR has helped identify attackers before they launch malware, pushing ransomware gangs to work more quickly and put more effort into hiding themselves. Organizations and MSPs need additional support and continuous coverage to outmaneuver today’s criminals.”
Smaller ransomware groups are becoming more prolific
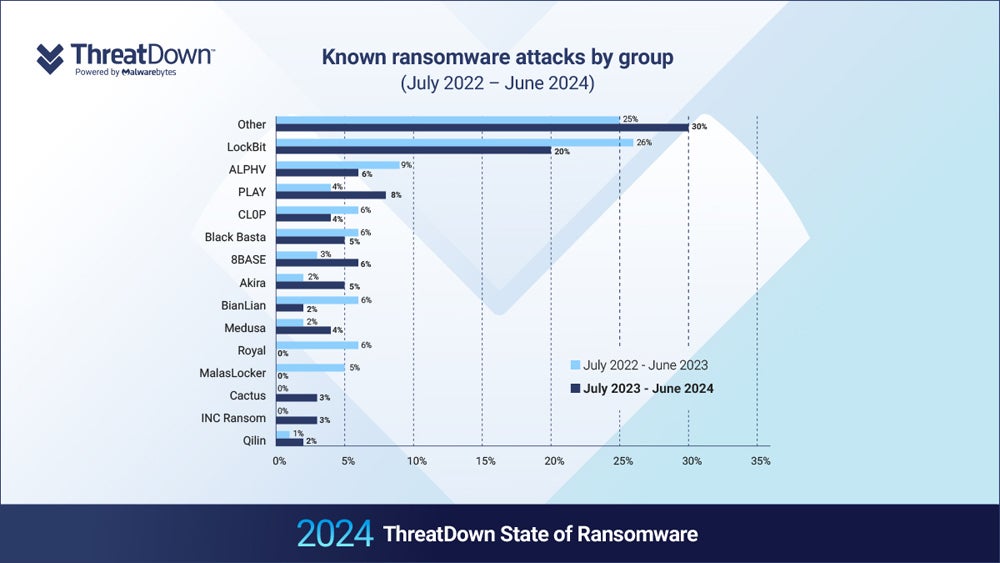
The proportion of ransomware attacks being conducted by small gangs outside the top 15 most active groups rose from 25% to 31% last year. This indicates that staging ransomware attacks is becoming more accessible to less experienced attackers.
In January 2024, the U.K.’s National Cyber Security Centre warned that the threat of ransomware was expected to rise even further due to the new availability of AI technologies decreasing the barrier to entry. For example, Google Cloud analysts said that generative AI may be used in call centres running ransomware negotiations.
The Malwarebytes report also found that the proportion of ransomware attacks that dominant ransomware-as-a-service group LockBit claimed responsibility for decreased from 26% to 20% over the past year, despite carrying out more individual attacks.
SEE: 94% of Ransomware Victims Have Their Backups Targeted
LockBit’s dominance may have taken a hit after the U.K. National Crime Agency’s Cyber Division, the FBI, and international partners successfully cut off access to its website, which had been used as a large ransomware-as-a-service storefront, in February.
However, a few days later, the group resumed operations at a different Dark Web address and continues to claim responsibility for global ransomware attacks.
ALPHV, the second-most prolific ransomware group, also created a vacancy after a sloppily executed cyber attack against Change Healthcare in February. The group did not pay an affiliate their percentage of the $22 million ransom, so the affiliate exposed them, prompting ALPHV to fake a law enforcement takeover and cease operations.
Furthermore, a recent report from WithSecure found that, of the 67 ransomware groups it tracked in 2023, 31 are no longer operational as of Q2 2024. A report from NCC Group also noted a year-on-year decrease in ransomware attacks in both June and July this year, which experts linked to the LockBit disruption.
These observations suggest that law enforcement takedowns, like those of ALPHV and Dispossessor, are proving effective against the more-established gangs while simultaneously opening up new opportunities for smaller groups.
The Malwarebytes report authors wrote, “With ALPHV gone and LockBit’s future uncertain, other gangs are certain to be trying to attract their affiliates and supplant them as the dominant forces in ransomware.”
SEE: Report: Impacts of AI on Cyber Security Landscape
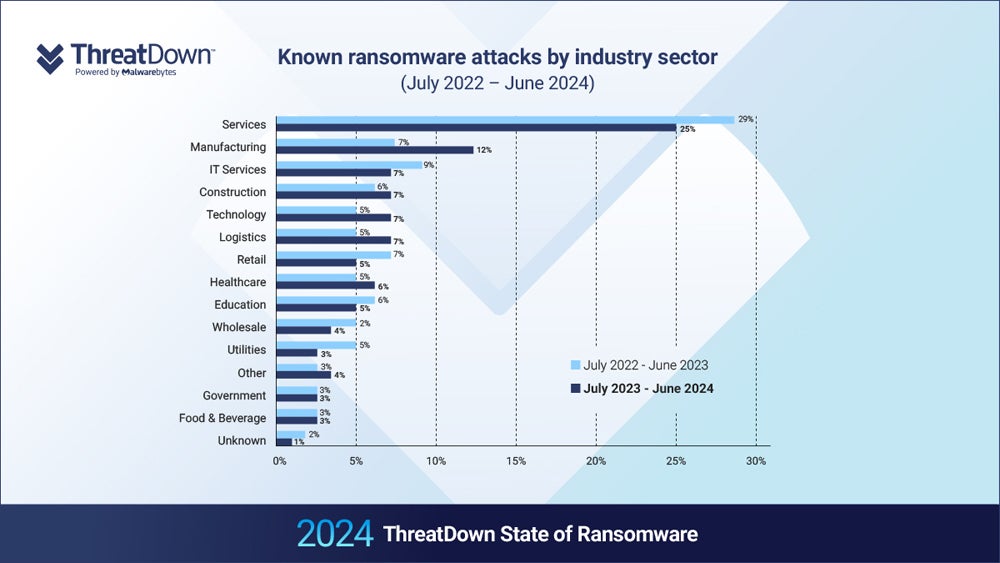
Top targeted industries for ransomware in the U.S. and worldwide in 2024
Ransomware is a growing threat all over the world, with the number of enterprises attacked increasing by 27% in 2023 and payouts exceeding $1 billion (£790 million) for the first time. Globally, ransomware damage costs are predicted to exceed $265 billion by 2031.
According to the Malwarebytes report, the services industry is the worst affected, accounting for almost a quarter of global ransomware attacks. Compromising critical national infrastructure can lead to widespread disruption, making it a prime target for ransomware.
In May, the U.K.’s National Cyber Security Centre and other international cyber authorities, including the FBI, warned about cyber attacks targeting providers of operational technology. The advisory came in light of “continued malicious cyber activity” against water, energy, and food and agriculture businesses between 2022 and April 2024.
SEE: How hackers infiltrate critical infrastructure
The report also found that, while the U.S. accounts for nearly half of all ransomware attacks worldwide, it takes on 60% of global attacks on the education sector and 71% of them on healthcare.
This could be related to its highly privatised, and therefore wealthy, healthcare system and higher education institutions, as well as strict regulations such as HIPAA and FERPA that pressure organisations into paying the ransom to avoid fines.
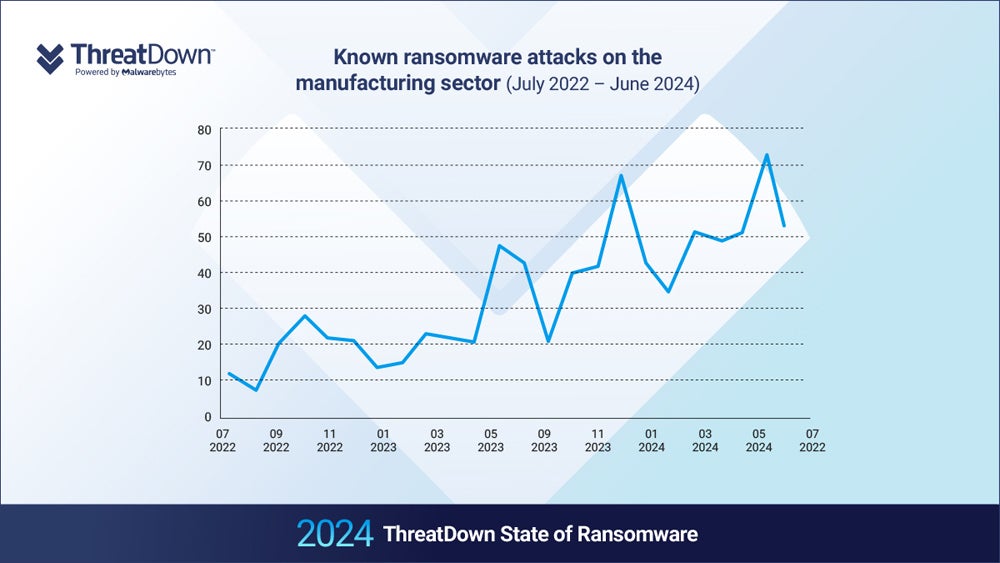
The global manufacturing sector saw a 71% year-on-year increase in ransomware attacks, corresponding with increasing software spend in the sector.
“The most likely explanation therefore is that the number of available targets in the manufacturing sector has increased over the last two years, perhaps because of increasing digitization within the sector,” the authors wrote.
Tactical shifts of ransomware attackers in 2024
The ThreatDown MDR team noted a rise in living-off-the-land techniques being used by ransomware gangs, such as LockBit, Akira, and Medusa. Living-off-the-land is the use of legitimate, pre-installed tools and software within a target environment during an attack to help evade detection.
This can reduce the overall complexity of the malware by allowing the attacker to weaponize existing features that have already been security tested by the organisation, as well as making detection and prevention more challenging. The M-Trends 2024 report, from Google subsidiary Mandiant, also noted an increase in living-off-the-land attacks back in May.
The M-Trends report also found that the median dwell time — the amount of time attackers remain undetected within a target environment — of global organisations fell from 16 days in 2022 to 10 days in 2023.
Malwarebytes’ report indicates this faster attack timeline too, with ThreatDown Incident Response data showing how the entire ransomware attack chain, from initial access to data encryption, has reduced from weeks to hours.